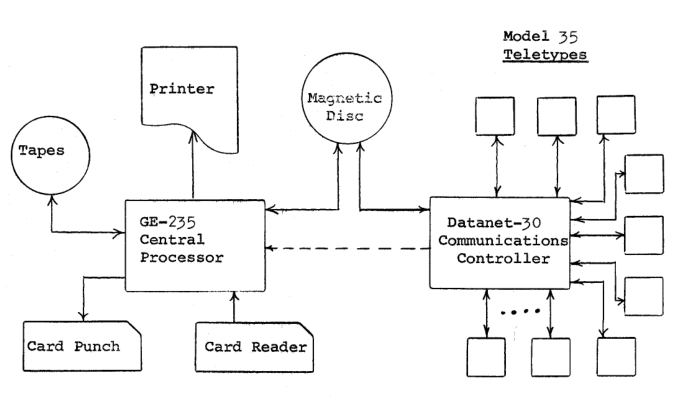
One important point when dealing with Algol is different levels or
representations of the language: there is one for the spec, one for
printed programs and one for the machine implementation. As an
example, to raise a to the power b:
- Spec: a ↑ b
- Printed: ab
- Machine - Dartmouth:
a ^ b
- Machine - IBM:
a ** b
We'll use the printed form in this article and the Dartmouth machine
form for code examples.
Keywords are in bold lower case in the printed form (eg integer).
Dartmouth uses upper case (eg INTEGER). (IBM used quotes, eg
'INTEGER', which must have been a pain to type).
Here's an example program that will print Hello World 5 times
10 BEGIN
20 INTEGER I;
30 FOR I := 1 STEP 1 UNTIL 5 DO
40 PRINT("HELLO, WORLD")
50 END PROGRAM
The line numbers are not part of Algol but are needed for the Dartmouth
program editor.
Statements are grouped into blocks, separated by semicolons; the last
statement in a block does not need a semicolon.
Variables are typed (real, integer, boolean); strings are
allowed only as constants.
Algol has no standard I/O - reflecting how different each computer was
at that time, it was up to the implementation to add this. Dartmouth
Algol uses print much like BASIC for output.
Let's exercise Algol further by implementing the TPK algorithm.

 Detail from the cover of the original BASIC manual. Source:
Detail from the cover of the original BASIC manual. Source: