The CTSS supervisor
The supervisor is at the heart of the CTSS system and operates similarly to what we'd call a kernel today. Let's look at each of its functions, comparing them to modern systems to get a feel of what is different.
Hardware
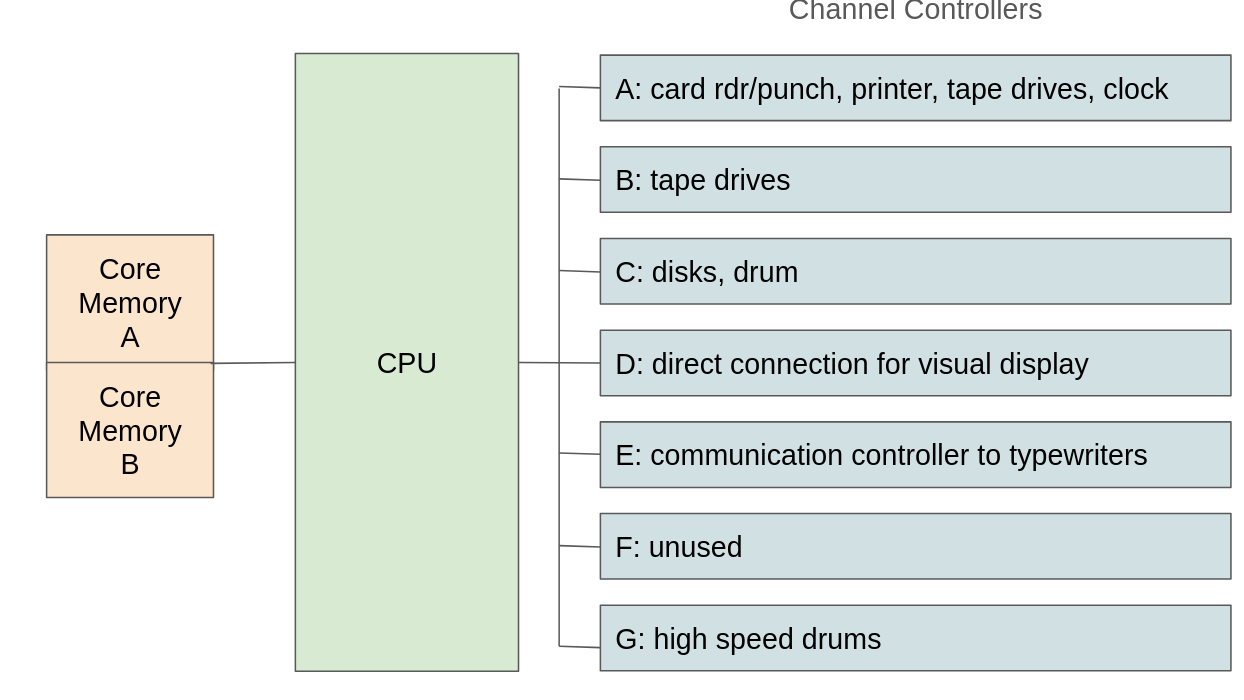 Diagram of CTSS hardware. Source: Rupert Lane. License: CC0.
Diagram of CTSS hardware. Source: Rupert Lane. License: CC0.
The hardware controlled by CTSS changed over its lifespan. This is the setup that matches the CTSS source code used in the emulator. Most I/O work was done by channel controllers which offloads some of the work from the CPU. Each channel can have up to 10 devices connected to it. User programs cannot access components directly, they need to go through supervisor services.
Memory
There are two separate 32kW banks of memory, known as Core Memory A and B. Note each word is 36 bits, so that's the equivalent of around 147 kilobytes in each bank. As the 7094 can only address 32kW at a time, these are switched between as needed. The supervisor sits in Core A at all times. User programs are brought into Core B as requested by the user, and may be swapped out to drum or disk as CTSS schedules other tasks to run. The maximum memory available to a task is 32kW and there is no concept of virtual memory; however several smaller tasks can be in memory at the same time.
Tasks
A fixed maximum number of users can be logged in at any time (30 is the limit on the emulated system). Each user can only have one task active, so could not login twice simultaneously or create (fork) a new task while an existing one is running.
There is no equivalent to a shell as a separate user program. Logged
in users type in commands which are processed by the supervisor.
Commands and their parameters can each be up to 6 characters long.
Commands can be either system programs (eg LISTF) or user created
programs and are treated the same way: the supervisor will load the
program into core B and transfer to it. Once a task is completed,
control is returned to the supervisor.
Each task can be in a particular state, such as working, waiting for I/O etc. Two special states refer to the task after it is completed: dormant means the program has finished but is still in core so can be restarted or the machine state analysed. Dead means the program is out of core.
Scheduling
The scheduling algorithm for CTSS evolved over time as experience was gained using the system. As of the later system it had nine priority queues, ordered so that smaller or newer tasks would get a small amount of CPU time quickly, and longer running tasks would run less frequently but get more CPU time when it was being run.
It is also possible to run background tasks at a lower priority. This included jobs submitted by users from the online system (called FIB jobs) as well as non-time-sharing aware jobs, such as batch or standalone 7090 programs. This ability to run pre-CTSS jobs explains the 'Compatible' in the OS's name.
Protection
CTSS applies relocation to each task so it can be placed anywhere in memory without the task being aware of its physical position. The system also keeps track of what areas of memory the program is using, so any access outside of there leads to a protection violation and the program being terminated.
Further reading
The original paper by Fernando Corbato is available at the ACM. It describes an earlier version of the system we have today, but also includes information on why the system was developed.
The CTSS Programmer's Guide section AA gives more detail on the supervisor.
Bob Supnik's analysis of CTSS hardware was also useful in understanding how CTSS worked and is emulated.
Questions, corrections, comments
I welcome any questions or comments, and also especially any corrections if I have got something wrong. Please email me at rupert@timereshared.com